You may have heard a lot about decentralized identifiers (DIDs) in articles and videos about decentralized identity, blockchain, or digital credentials, but don’t really know how they work. We’ll go over everything you need to know about DIDs and why they are so essential in the game-changing Verifiable Credential technology that Dock has been building since 2017.
TL;DR
- There are many problems with using centralized identifiers like emails and usernames to access websites and apps. Issues include lack of ownership and control of data and increased risk of data breaches. Decentralized identifiers can effectively solve many of these problems.
- Decentralized identifiers (DIDs) are globally unique identifiers made up of a string of letters and numbers that act like an identifying address on a blockchain and are independent of any organization.
- DIDs can be used to digitally sign and issue Verifiable Credentials like educational certificates, and to verify credentials instantly.
- Decentralized Identifiers contain cryptographic key pairs and are fully under your control.

Introduction
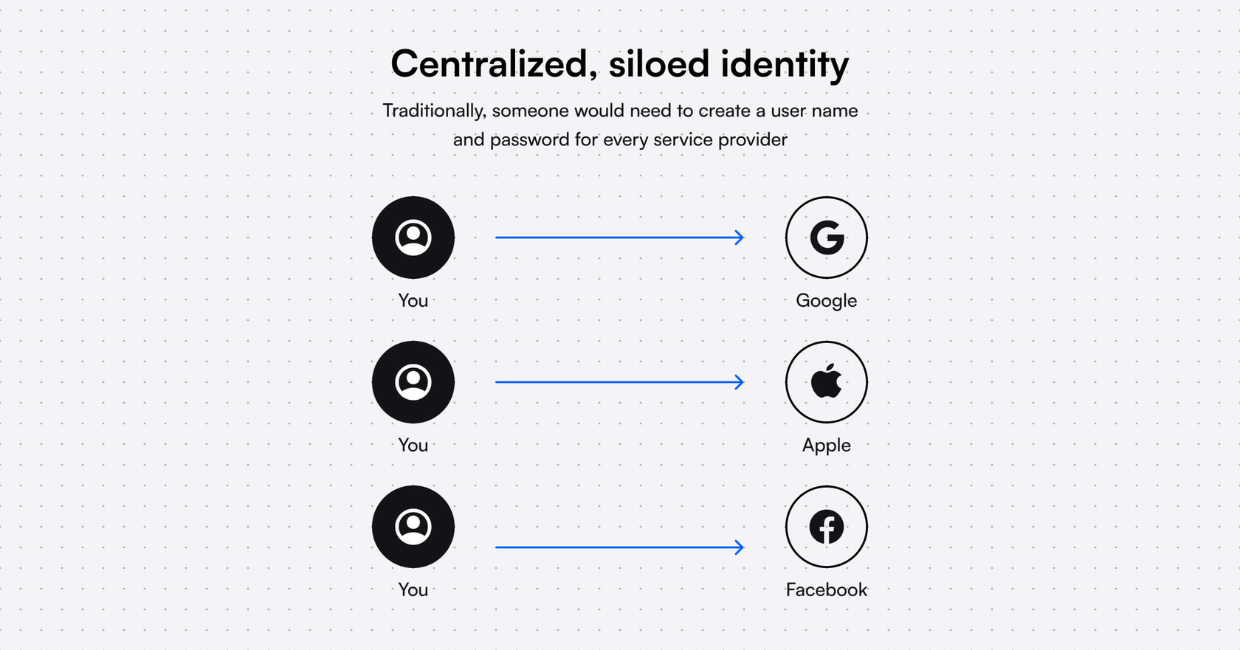
Until now, we have been dominantly using emails, usernames, and passwords to access websites, apps, and services. These are called centralized identifiers.
These are several problems with centralized identifiers for:
But decentralized identifiers can solve all of these problems.
What Are Decentralized Identifiers (DIDs)?
Decentralized identifiers (DIDs) are a way to identify yourself on the internet without using a central authority, like a government or a company. Think of it like a digital passport that you control, rather than one that's issued to you by someone else. With a DID, you can prove who you are online without having to give your personal information to a bunch of different websites or apps. It's like a digital version of a driver's license that can only be used by the person it's issued to.
Key features of DIDs:
- Are created and managed completely by the user (individual or organization) without depending on any third party
- Allow the owner to securely prove control over them
- Don’t contain any personal data or wallet information
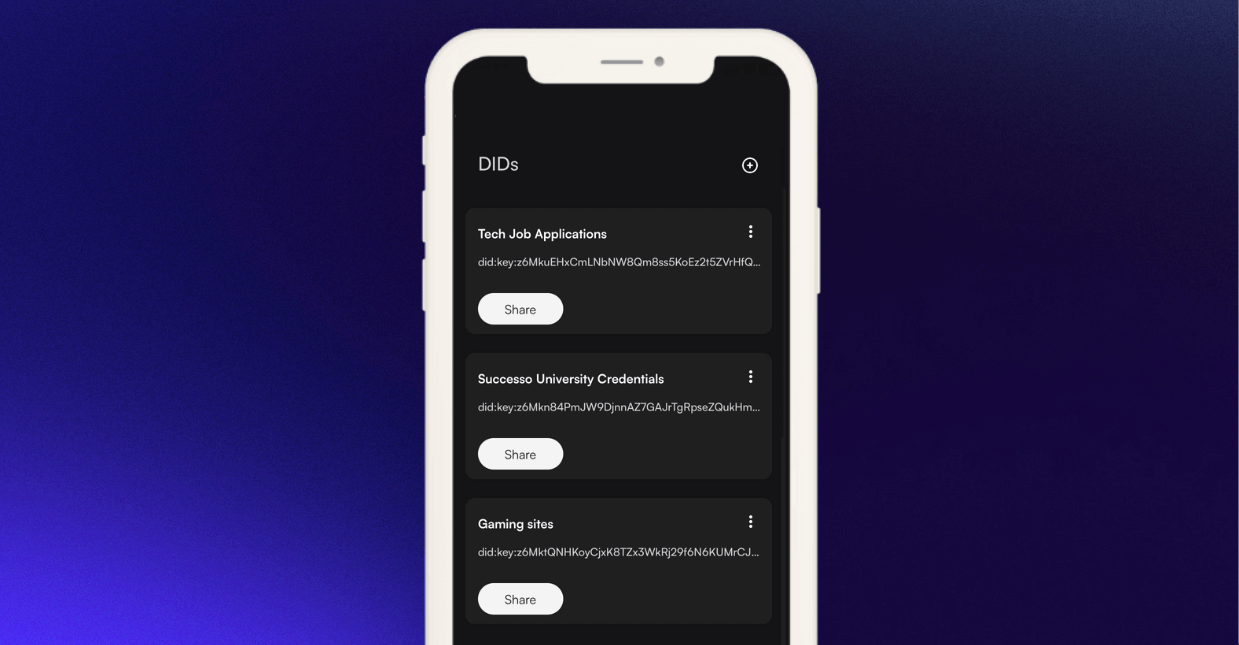
Here’s an example of a Dock DID:

DIDs can be easily created with the Dock Wallet and Dock Certs platform.
We have different online profiles to show various aspects of our lives such as having a Facebook account to share updates mainly to our friends and family and LinkedIn to show your work and educational experience to our professional network as well as employers. DIDs can be used in the same way where people can create as many DIDs as they want for different purposes.
For example, you can have a DID for different interactions:
- DID 1: Online gaming sites
- DID 2: For educational and training credentials such as a university degree, Project Management Certificate, and health and safety training certificate
- DID 3: To hold different types IDs like state ID and driver’s license
- DID 4: Online shopping websites
- DID 5: Crypto investment platforms and services
3 Pillars of Self-Sovereign Identity
Decentralized identifiers are one of the three pillars of Self-Sovereign Identity which is a model that gives individuals and organizations full ownership and control of their digital identities without relying on a third party.

Self-Sovereign Identity pillars:
- Blockchain: A decentralized database that is shared among computers in the blockchain network that records information in a way that makes it very difficult to change, hack, or cheat the system.
- Decentralized Identifiers (DIDs): Verifiable identifiers created by the user, owned by the user, and independent of any organization.
- Verifiable Credentials (VCs): Digital cryptographically-secure versions of paper and digital credentials that people can present to verifiers such as an employer, government agency, or party in a supply chain.
Cryptography is an area of computer science that focuses on transforming data so that it can’t be accessed by unauthorized users and is used to protect digital data. Cryptography is what makes Verifiable Credential and blockchain technology secure.

World Wide Web Consortium’s Decentralized Identifier (DID) Standards
The World Wide Web Consortium (W3C) is an international organization that creates standards for the World Wide Web and has a goal to create technical standards as well as guidelines for web technologies around the world. They created the URL and Verifiable Credentials standard among others.
W3C established Decentralized Identifiers (DIDs) v1.0 which describes the technological details and standards that organizations creating DID solutions can follow. W3C describes DID as being “A new type of identifier that enables verifiable, decentralized digital identity.” Learn more about decentralized identity.
Benefits of Decentralized Identifiers
DIDs enable the following for organizations, individuals, and developers:
Centralized vs. Decentralized Identifiers
These are the key differences between centralized and decentralized identifiers:
Verifiable Credentials System
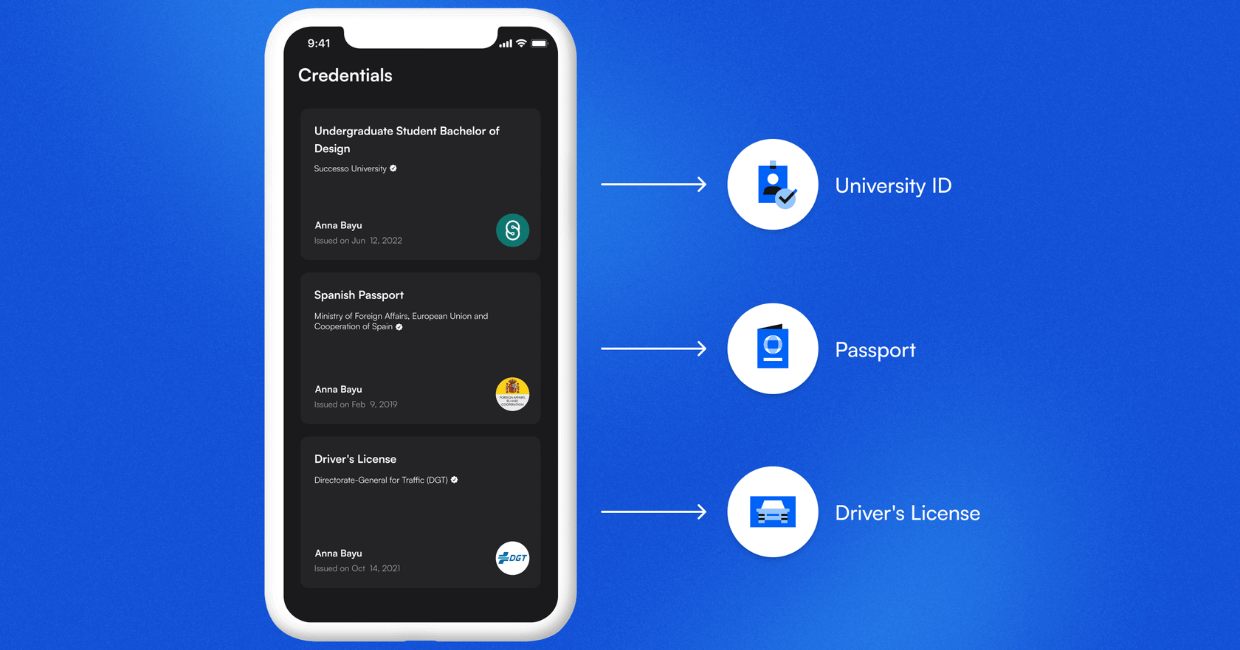
When we want to make claims about ourselves like our experience, education, and training, we use physical cards or digital documents such as a university degree or certificate. But these documents can be easily forged and verifiers like employers often can’t tell if it is real or fake without contacting the issuing organization like a college or training institution, which can take weeks or even months. Fake diplomas alone are a billion dollar industry and the problem is only growing.
Decentralized identifiers enable organizations and people to securely store their Verifiable Credentials that can be checked anywhere at any time. Verifiers can simply scan a QR code or use a simple verification tool that instantly confirms the authenticity of the credential.
Here are some examples of documents that can be issued as Verifiable Credentials:
Decentralized Identifiers and Blockchain

Before going deeper into DIDs, it’s important to have a basic understanding of what a blockchain is and how it works. DIDs can be stored on a blockchain in order for people and organizations to efficiently share data and verify credentials.
A blockchain is a digitally distributed database that is shared among computers in a blockchain network and records information in a way that is tamper-resistant.
Key benefits of blockchain:
- Strong security: Uses cryptography to enable privacy and security.
- Tamper-resistant: In a blockchain design, each block has a hash (combination of letters and numbers unique to that block) that acts like a digital fingerprint and each block contains a hash of the previous block. The importance of this is if someone tried to manipulate the data, the hash would change and everyone in the network would know about this. This block would be rejected and not be added to the blockchain.
- Distributed: Every authorized person in the blockchain network gets a copy of the blockchain and can see the transactions.
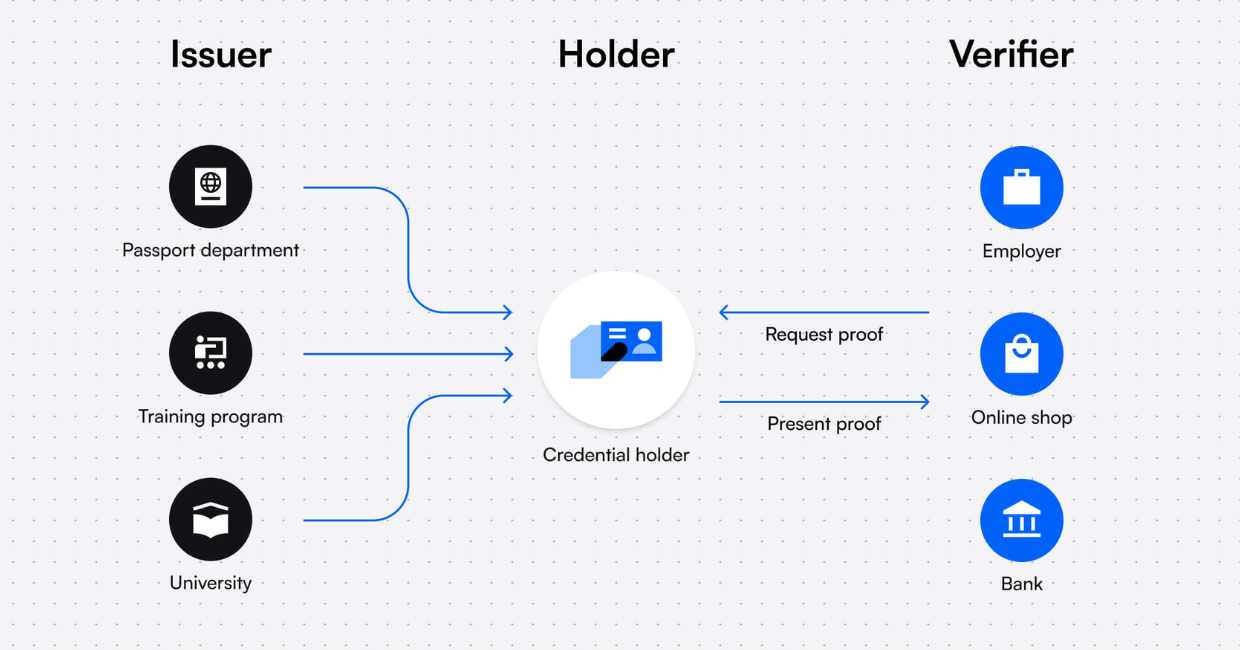
The Role of DIDs In the Verifiable Credentials System
Whenever an organization issues someone a Verifiable Credential, their public DID is attached to that credential. Because the public DID (and issuer’s public key) is stored on the blockchain, whenever a party wants to verify the authenticity of the credentials, they can check the DID on the blockchain to see if it was really the issuer’s private key that signed the Credential. This is done without having to contact the issuing party. With traditional verification processes, including phoning and emailing issuing organizations, it often takes days, weeks, or even months to validate credentials.
In the Verifiable Credentials system, there are three main parties:
- Issuer: Organization or party with the authority to issue Verifiable Credentials that confirm a claim. Issuers have their own unique DID.
Examples of parties that issue documents as Verifiable Credentials:
- Government inspector that issues a document that confirms that the produce meets quality standards
- University issuing degrees
- Employer issuing employee titles and company ID numbers
- Lab issuing a report on patients’ blood test results
- Safety training organization issuing certificates to participants who successfully pass their course
- Holder: Organization or individual who owns the credential. A holder has their own DID.
- Verifier: The person or organization validating the credential.
Examples:
- Food buyer who wants to ensure that products are certified organic
- Employer that wants to ensure that interviewees have a mechanical engineering degree
- Customers who want to confirm that the luxury product they bought is authentic and not a knock-off
It’s important to know that Verifiable Credentials, confidential data, and personal information are not stored on the blockchain. The blockchain only stores a record of DIDs. Users can, however, create a hash on the blockchain that is time stamped and acts like a digital fingerprint to prove the existence of the credentials associated with a DID where the data is securely encrypted. The process of creating a digital fingerprint of data and writing it on a blockchain is called anchoring and you can learn more about that here in the section “How to Show the Proof of Existence of Verifiable Credential Data and Files With Dock’s Blockchain.”
How to Verify Credentials With Decentralized Identifiers
Organizations can easily confirm the authenticity of users' digital credentials in seconds using Dock Certs and the Dock Wallet. The verification system is powered by blockchain technology which ensures speed and reliability. Dock's tools are equipped to detect any fraudulent credentials, providing verifiers with the peace of mind that the information being presented is genuine. Verification can be done through the web or wallet-to-wallet (online and in person).
Benefits of Verifying Credentials Instantly for Organizations
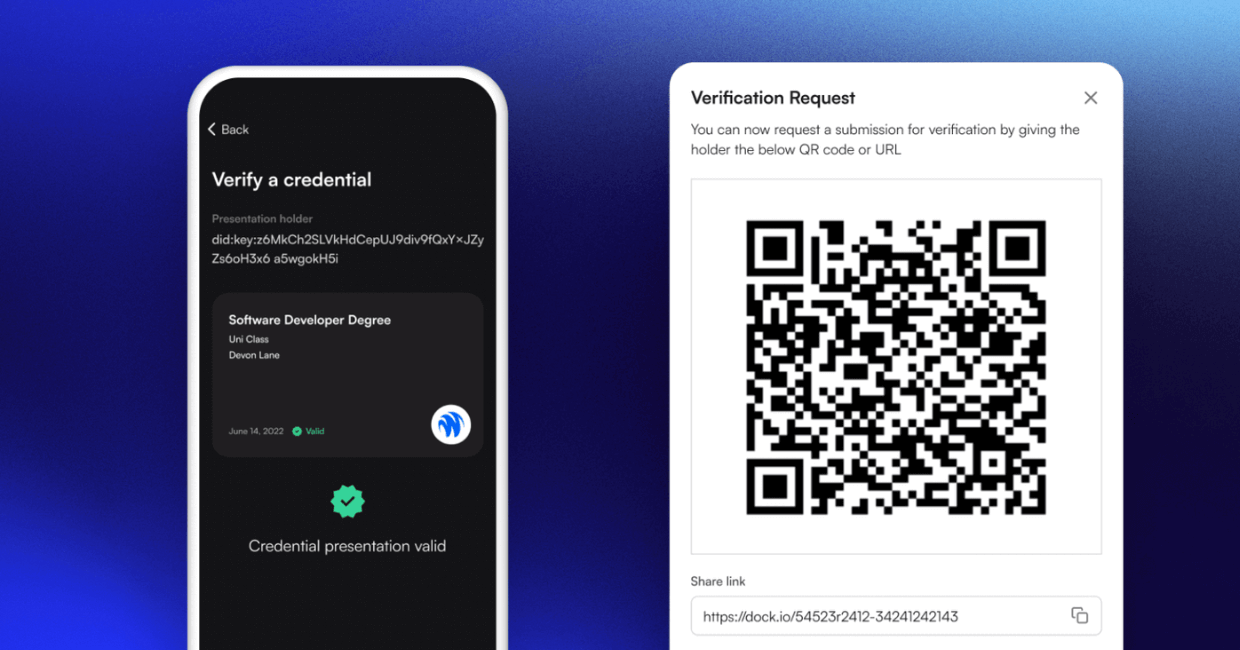
- Verify digital credentials in seconds and eliminate traditional verification methods that can take days, weeks, or even months
- Prevent credential fraud
- Improve the verification process to save time and reduce costs by eliminating manual and inefficient methods
- Meet data security regulations
- Enhance operational efficiency
- Reduce the risk of liabilities, penalties, legal proceedings, injuries, and death by ensuring that only qualified individuals are hired
Benefits of Verifying Credentials Instantly for Individuals

With the Dock Wallet, people can:
- Enjoy increased control and security over their personal data by being able to selectively share specific aspects of their credentials with a verifier. They can, for example, choose to only show their name and email address while keeping other credential information like their birth date or address private.
- Effortlessly share their credentials directly from their phone.
- Decrease the likelihood of unauthorized access to their data by only providing a verifier with necessary information while maintaining complete control over who has access to their information.
Complete Verification Guide
Click here for the step by step guide on how to verify credentials with Dock Certs and Dock Wallet.
Private vs. Public Decentralized Identifiers
Private DIDs can be exchanged between two parties to create a secure channel that no unauthorized person or party can access in that channel. Private DIDs are useful for organizations that need to share confidential information such as between executives of a company or lawyers within a firm working on client cases.
Public DIDs are beneficial for parties that need to be publicly identifiable such as a government department that issues IDs for citizens, players in the supply chain (producers, manufacturers, distributors, etc.), or health care providers.
Difference Between Public Keys and Private Keys That Come With DIDs

Every DID that is created by the user comes with a private and public key pair and DIDs can have multiple pairs. A key is a string of letters numbers that aren’t identifiable and you can think of a key being like a password.
Private key: This key enables a user to digitally sign documents, prove ownership, and give consent to share selected data. This key should never ever be shared with anyone because it provides access to all of your information. Think of this key being like a physical key to a vault with all of your valuable assets.
Public key: This key can safely be shared with anyone you choose to give information to. Think of it like an email address that people can send information to. The public key is what enables a verifier like a company to check who issued a Verifiable Credential without having to contact the organization because the issuer’s DID is on the blockchain.
To use another analogy, let’s say you are the owner of a company website with access to all of the permissions and features. No one will know the master password that gives full control over the site. The master password is like the private key.
But of course, because you have employees, you want to give them limited permissions to edit some sections of the site. So you send them an invitation link with specific permissions. This invitation link is like the public key.
To enhance security, think about someone using the same password like “foodie2010” for 20 different websites. This is not secure and this makes it easier for hackers to potentially steal your information. It’s better to have long and complex passwords for each site. Similarly, it’s good practice to generate new keys when you share information with a different party, which you can conveniently do with the Dock Wallet phone app.
Example of How Decentralized Identifiers Work In the Verifiable Credentials System
Here’s an example of how public and private keys work:
- Issuer: Government inspector certifying labor conditions in a clothing factory
- Holder: Production factory
- Verifiers: Distributor, retail shop, and customers
1. A clothing company in Denmark specializes in providing ethically-made clothes by producers that pay workers a living wage and healthy working conditions. Their customers have been asking for more information about product origins and want to buy products made by people in good working conditions.
2. The production factory, inspector, and clothing company each have a unique DID that was easily created using the Dock Certs platform. All of their DIDs are stored securely on the blockchain.

3. The government inspector evaluates the factory’s working conditions, worker pay, and other details. The factory meets the labor standards and the inspector uses his private key to sign and package all of the relevant information as a Verifiable Credential that can be checked anytime by verifiers.
Thanks to blockchain and Verifiable Credentials technology, verifiers never have to waste time and money contacting the inspector regularly to ensure that the products were made in good working conditions because the inspector’s DID and associated public key is on the blockchain.
4. When the distributor receives a shipment of clothes, it comes with a QR code connected to the inspector’s DID and associated Verifiable Credential. The distributor scans the QR code with their phone and instantly sees that the clothes meet labor standards.

5. When the store in Denmark receives the next shipment of clothes, the manager scans the QR code to check the Verifiable Credential issued by the inspector.

6. The store adds a QR code on the online shop and in the physical store for customers to learn more about the project origin and details. When the customers scan the QR code, they can see the details about the factory where the clothes were made. The customers feel great about buying from a socially responsible company and the business gains more trust while enhancing their reputation.
Use Cases For DIDs
There are a growing number of applications for DIDs. Here are just a few of many examples of how DIDs can help organizations increase operational efficiency and empower individuals to completely own and control their credentials and digital identity.
Transferring sensitive patient information between health providers
An online health data management provider integrates DID and Verifiable Credential technology to enable health providers to share patient data in a secure way that is compliant with privacy regulations and has patient consent.
Let’s say there’s a patient who is issued a DID that is registered on the health platform. Every time that patient goes for a blood test, the results are issued as a Verifiable Credential and associated with their DID. Whenever that patient receives cancer treatment, the report that has the details of their progress is issued as a Verifiable Credential. Each health provider will have their own unique DID. If the patient gives consent for relevant health providers to view this diverse data, then their family doctor, cancer specialist, and pharmacy can check their VCs anytime to see patient details.
Instantly verifying credentials in the construction industry
Many construction companies often need to hire workers quickly and don’t have the time or tools to check every job applicant’s credential, which can put other staff and the public at risk. A construction training institute can issue fraud-proof certificates to graduates that they can store on their phones. The training institute, holder, and hiring construction company will each have a DID.
Rose goes to a construction company’s office to apply for a job and presents her Verifiable Credential from her phone. The hiring manager simply scans a QR code that shows she is a qualified worker because the company trusts the training institute as an issuer, whose DID is on the blockchain.
Tracking someone’s training within a company
A company uses decentralized identifiers and Verifiable Credentials to track their employees’ skill development. Every employee has a DID that is registered with the company. Every time someone finishes a training program like “Workplace Diversity” or “Advanced Platform Training,” they will issue a Verifiable Credential for the team member that can be checked anytime. HR can use this for their performance reviews and evaluations for raises.
Ensuring the authenticity of a product
Let’s say Mary is looking for a special edition collectible card. She finds an online store that uses globally-recognized identifiers for all of their collectible products so Mary is assured that she’s getting an authentic product. Whenever the product changes owner, the title transfer is issued as a Verifiable Credential all the way back to the statement of authenticity from the original manufacturer. Each of the title transfers can be verified instantly because they were signed with the public DIDs of the buyer and seller.
Issuing IDs for citizens
A government department can issue digital state IDs as Verifiable Credentials that holders can securely store in their phone wallet app in addition to their physical card. Jada’s Dock wallet provides the public DID to authenticate her identity and the government issues the VC to her DID. She can conveniently carry her digital state ID everywhere with her phone.
Importing products
Lee is the operations manager in Singapore for an import company that specializes in high end furniture manufactured in Italy. Lee works with many different products and manufacturers. To efficiently manage all of the information on materials, transportation, and costs, he registers a DID with the customs department that issues a digital license as a Verifiable Credential to the company. The digital license proves the company is an authorized importer.
With the company DID, Lee digitally signs and delegates the digital license to the manufacturers, which authorizes them to send products to Singapore. Any verifier, including the Singaporian customs department, can instantly check the original license and chain of authorizations. When the furniture arrives in Singapore, the customs department can efficiently verify that this batch of products is officially licensed.
How to Manage and Create a Decentralized Identifier
Organizations and individuals can easily create DIDs with our user-friendly, intuitive, and no-code Dock Certs platform. See our step-by-step guide on how to easily create DIDs in the section “How Do You Create Decentralized Identifiers?”
Manage DIDs With the Dock Wallet
The Dock Wallet enables users to securely create, export, import, edit, delete, and share their DIDs. With the wallet, you can take your Verifiable Credentials anywhere and fully own, control, and manage your data.
Dock DIDs can have multiple keys that can be used for different purposes. For example, an issuer like a company may use their DID these reasons:
- Issue Verifiable Credentials to employees
- Authenticate credentials from manufacturers
- Engage in secure communication with the company’s lawyers
- Remove credentials from contractors when their work has completed
It is ideal to have separate keys for each of these purposes so if one key is compromised or lost, the other functions aren’t affected.
Learn more about Dock DIDs supporting multiple key pairs.
Conclusion
We mainly use centralized identifiers like emails, usernames, and passwords to access websites and apps. But these identifiers have many problems for individuals, organizations, and developers including data being collected and shared to other parties without people’s knowledge, data tracking, and lack of control of data. Fortunately, decentralized identifiers (DIDs) can solve all of these problems.
DIDs play a key role in the Verifiable Credentials system and these are the key benefits for:
- Organizations: Efficiently issue fraud-proof credentials and verify credentials instantly
- Individuals: Full ownership and control of data while preventing data tracking
- Developers: Eliminates the need for passwords and they can request data directly from users rather than using third-party authentication like Google
Learn More
- Blockchain and Health Care: BurstIQ Use Cases
- How to Prevent Certificate Fraud
- How to Prevent Supply Chain Fraud
- Verifiable Credentials
- Blockchain Identity Management
- Data Compliance
- Digital Credentials
- Decentralized Identity
About Dock
Dock is a Verifiable Credentials company that provides Dock Certs, a user-friendly, no-code platform, and developer solutions that enable organizations to issue, manage and verify fraud-proof credentials efficiently and securely. Dock enables organizations and individuals to create and share verified data.







