TL;DR
- Blockchain verification is a process that provides a tamper-proof and efficient way to verify credentials
- For organizations, blockchain verification improves trust, reduces fraud, streamlines the verification process, and lowers verification costs
- For individuals, blockchain verification empowers them with control over their personal information, ensures privacy, and enables seamless portability of credentials
- Blockchain verification technology can be integrated in diverse industries including education, healthcare, workforce, and construction
- Verifiable Credentials, decentralized identifiers (DIDs), and digital wallets are key technology tools in the blockchain verification system
What Is Blockchain Verification?
Blockchain verification is a secure way to confirm the authenticity of credentials using blockchain technology. Blockchain verification is like a public, secure stamp of approval for digital information.
Imagine blockchain as a digital ledger, like an accounting book, but one that everyone can see and no one can alter once information is added. Each entry in this book is a “block”, and all these blocks link together in a “chain”, hence the name "blockchain". What makes this technology special is that every time a new block is added, it's approved by a network of computers. This makes the information in it very secure and tamper-proof.
With Dock, digital identifiers called decentralized identifiers (DIDs) can be added to the blockchain. Dock never adds Verifiable Credential or personally identifiable (PII) information on the blockchain to protect user privacy and data security. Our blockchain serves as a registry of issuer DIDs.
For example, your university digitally signs the diploma with their unique digital identifier (like a digital signature), issues it to you, and you store it on a digital wallet. If an employer wants to verify the authenticity of your diploma, because the university’s unique identifier (their issuer DID) is on the blockchain, the employer can instantly see that the diploma is valid and issued by the school.

Blockchain Verification System

There are 3 parties in a blockchain verification system:
1) Issuer: The entity that creates and provides digital credentials to individuals or other entities.
Examples of issuers:
- Universities issuing digital diplomas
- Governments issuing digital ID cards
- Companies providing certificates of completion for a training program
2) Holder: The person or organization that receives the digital credential issued to them.
Examples of holders:
- A graduate storing their digital diploma
- A citizen with a digital ID card
- An employee with a digital training certificate
3) Verifier: The party that checks or validates the digital credentials presented to them.
Examples of verifiers:
- An employer verifying a job applicant's diploma
- An airport security checking a digital ID
- Training platform validating a user's certification
How Long Does Blockchain Verification Take?
With the Dock blockchain, once someone sends their credentials to a verifier such as a company or government department, the information is verified instantly within seconds. With other blockchains, verification can be anywhere from seconds to hours.
Key Factors That Affect Blockchain Verification Times
Network congestion: The amount of transaction activity on the network can significantly affect the speed of blockchain verification. When there's high transaction volume, more time may be required to verify each transaction due to the backlog.
Block size: Different blockchains have different block sizes, and this can affect the speed of verification. A smaller block size means that less data is processed at one time, which can lead to faster verification times but might also lead to network congestion.
Complexity of the transaction: The complexity of a transaction, including the number of inputs and outputs, can also affect the time required for verification. More complex transactions require more processing power and thus more time.
Transaction fees: Higher transaction fees incentivize miners to prioritize certain transactions over others. Therefore, if you are willing to pay a higher transaction fee, your transaction may be verified more quickly.
Blockchain Verification Use Cases

Blockchain verification can be applied in a wide variety of sectors. Here are just a few of many examples:
Education
- Credential Verification: Educational institutions can issue digital degrees and certificates and the blockchain helps employers easily verify someone's qualifications without needing to contact the institution directly.
- Transcript Verification: Similar to credential verification, blockchain can secure and verify academic transcripts, reducing the possibility of fraudulent claims.
Health and Safety
- Identity Verification for Telemedicine: Verifying the identity of doctors and patients is crucial in online sessions. By using digital identifiers on the blockchain, patients can ensure they're interacting with a legitimate medical professional.
- Food Safety: Blockchain can be used to track and verify the journey of food items from farm to table. This can help identify the source of contamination in the event of a food safety issue, protecting public health.
Finance
- Identity Verification for Digital Banking: Digital banking can leverage blockchain to verify the identity of customers. This ensures that online financial transactions are made securely and both the bank and the customer are protected against fraudulent activities.
- Proof of Funds: When making large transactions or investments, proof of funds is often required. Rather than waiting for bank statements or letters, a blockchain-verified credential can instantly confirm the availability of funds, making transactions quicker and more efficient.
Why Blockchain Verification Is Needed
Blockchain verification leverages the power of decentralized networks to establish trust which greatly enhances the efficiency and reliability of data verification.
Problem With Traditional Verification Processes
1. Time-Consuming: Traditional verification methods often require a lot of manual labor. For example, if you're verifying academic credentials, it would require reaching out to the issuing institution, waiting for them to respond, and then cross-checking the details. Verification can take weeks to months because this dependence on third parties can cause delays and complicate the verification process.
Hundreds of thousands of qualified nurses in the US alone waited more than 6 months to receive their licenses from verification delays and even simple mistakes like misplaced files.
2. Expensive: This cost of verifying credentials with traditional methods increases with the number of verifications required. Organizations often need to dedicate significant resources, including hiring dedicated staff, to manage and conduct these verifications.
3. Risk of Errors: Since traditional verification methods are often manually conducted, they can be prone to human error. Misinterpretation of information, typing errors, or simple oversights can lead to inaccurate verification.
4. Vulnerable to Fraud: Physical documents can be tampered with or entirely falsified, making them unreliable. Even if an organization has robust fraud detection measures, sophisticated fraud can sometimes slip through.
6. Privacy Concerns: Traditional methods often require sharing personal information with multiple parties, increasing the risk of data breaches and identity theft.

Blockchain Verification Solutions

1. Instant verification: Organizations can check the authenticity of credentials immediately without needing to contact the issuing organization.
2. Lower Verification Costs: With blockchain, the need for intermediaries is eliminated. Data is verified by a network of computers on the blockchain, drastically reducing the financial resources needed.
3. Fraud-Proof: Blockchain verification combats fraud by making the data tamper-proof. This immutable nature of blockchain makes it extremely difficult to manipulate data or create false records, or issuer DIDs in this case, significantly reducing the possibility of fraud.
4. Reduces the Risk of Errors: Since blockchain is a form of digital ledger where information is recorded accurately and cannot be altered once entered, it greatly reduces the risk of errors that could occur during manual data entry or transmission. Every entry is verified by multiple parties on the network, further reducing the chance of mistakes.
5. Eliminates Dependence on Third Parties: Instead of relying on third parties for verification, blockchain uses a network of computers to validate and record transactions. This decentralization not only speeds up the process but also removes the risk of bias or manipulation from a single controlling party.
For example, an employer can verify the authenticity of an academic certificate instantly because Dock’s blockchain verification tech checks the university’s DID on the blockchain. If the university’s DID is on the certificate, the system knows that the certificate is genuine. If it isn’t, it means the digital certificate is fake. Without blockchain verification, the employer would have to call up the university to verify that the certificate is authentic.
How Dock’s Blockchain Verification Solution Works
Decentralized identifiers (DIDs), Verifiable Credentials, and a digital wallet are essential technology tools in the blockchain verification system.
DIDs
A decentralized identifier (DID) is a new type of digital identifier where you have a globally unique identifying address in the online world that enables you to fully own and control your digital identity and prove who you are for online transactions. Individuals and organizations can create and manage DIDs.
Unlike traditional identifiers like your username or email address, a DID is fully owned and controlled by the user without needing a central registry, identity provider, or certificate authority. No one can take it away from you, or forge it, because it's cryptographically secured.
Here is an example of a decentralized identifier created by an issuer:

Two Types of Dock DIDs
Dock offers two types of DIDs that can be used by holders and issuers:
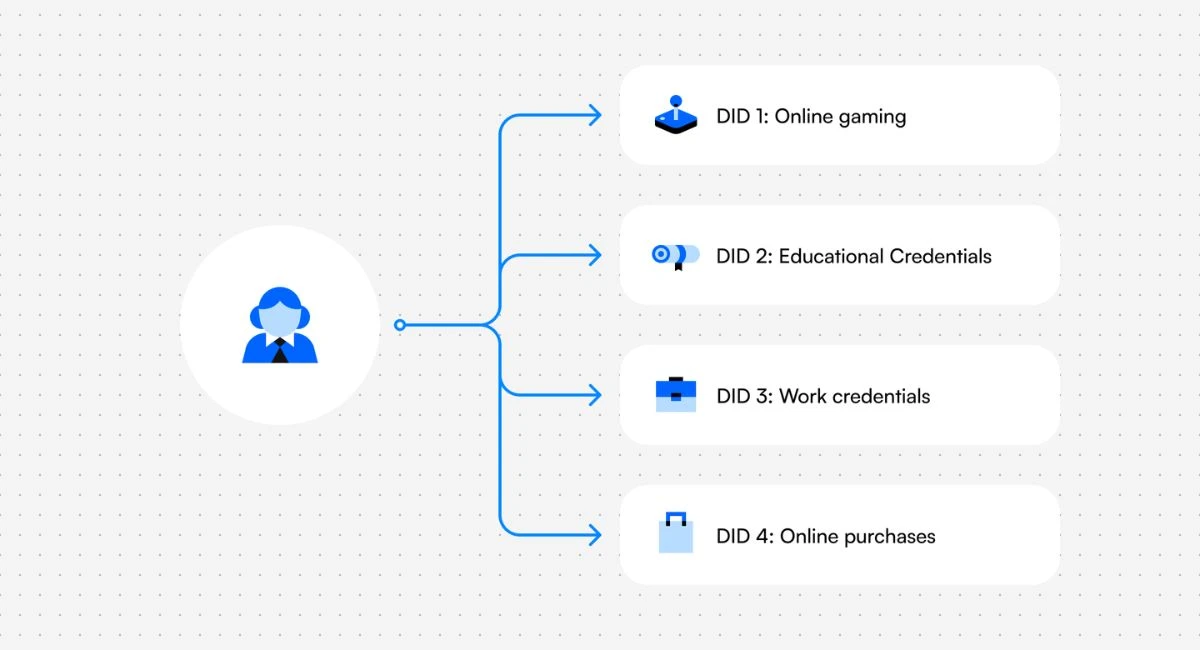
The benefits of issuers using multiple keys with did:dock
For issuers such as employers or universities, they can have one DID and multiple keys attached to the one issuer DID For multiple purposes. In the context of digital identity and DIDs, a "key" typically refers to a cryptographic key, which is a string of letters and numbers.
Let’s use an analogy to better understand how a “key” works. Imagine you have a big house with many rooms. Each room has a specific purpose, a kitchen for cooking, a bedroom for sleeping, a study room for work, and so on. To enter each room, you need a special key.
In the digital world, when we talk about a "key," think of it as these special keys that open doors to different rooms in your house. Each key has a unique purpose.
For example, Successo University can have one key that is just used to issue credentials and another key is used for authentication.
Verifiable Credentials
Verifiable Credentials are the digital equivalent of the physical credentials you carry in your wallet: driver's licenses, library cards, work IDs, etc. These credentials are issued by a trusted entity (like a government or university) and contain claims about a person or entity.
Dock Wallet for Organizations and Individuals
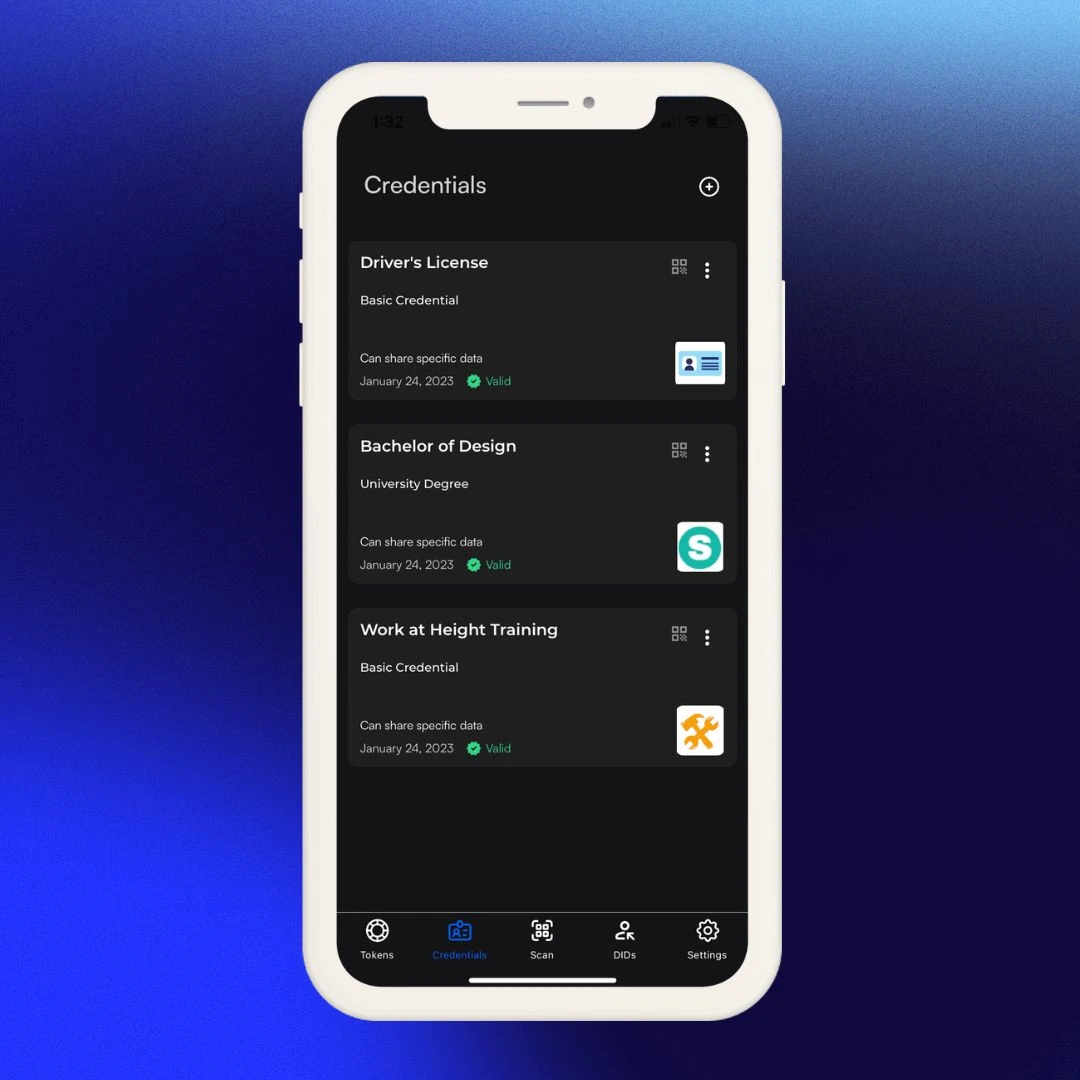
Non-Custodial Wallet
The Dock Wallet is a non-custodial wallet. The key benefits of a non-custodial wallet is that you have complete control over your digital assets, which means you don't have to rely on a third party to hold or protect them for you, and all of your assets are stored only on the device rather than a centralized storage system. You can send, receive, or trade your assets whenever you want, without needing permission from anyone else.
In contrast, a third-party custodial digital wallet provider has full access over your digital assets, which comes with these risks:
- Loss of control: When you use a custodial wallet, you hand over control of your private keys to the service provider. This means they have the power to access and manage your assets on your behalf. While reputable providers may have security measures in place, there is always a risk that they could misuse or mishandle your assets, intentionally or unintentionally.
- Security Breaches: Custodial wallets are attractive targets for hackers because they can potentially access a large number of users' assets in a single breach. If the service provider's security measures are compromised, it could lead to the loss or theft of your digital assets.
- Dependency on the Provider: You rely on the service provider to maintain the infrastructure, security, and overall operation of the wallet. If the provider goes out of business, changes their terms of service, or decides to discontinue their wallet service, it could disrupt your access to your assets or lead to a loss.

How Organizations Can Use the Dock Wallet for Blockchain Verification
1. Import credential verification requests from Dock Certs. Here is the complete step-by-step verification guide.

2. Conveniently share verification requests as a QR code from the wallet.

3. Instantly verify credentials wallet-to-wallet in person or online.
How Individuals Can Use the Free Dock Wallet
- Fully own and control your digital identity profiles by only presenting your credentials whenever you choose. Get the Dock Wallet on Apple or Android.
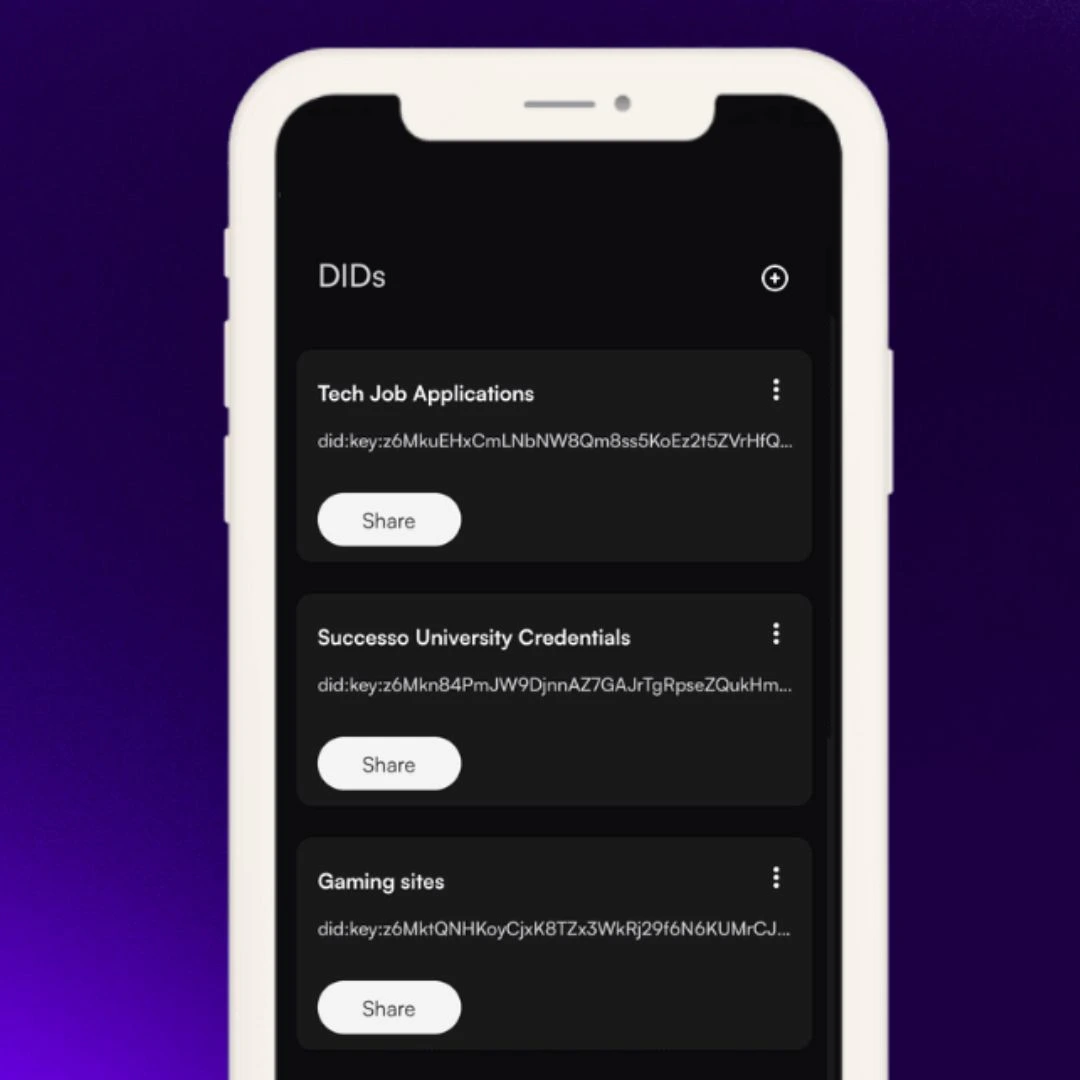
2. Manage your Verifiable Credentials and share only relevant data from verifiers instead of presenting a whole credential.

Why Dock Never Stores Verifiable Credentials on the Blockchain
There are several benefits to not storing Verifiable Credentials on Dock’s blockchain:
1. User Privacy
Because Dock’s system incorporates privacy by design, we never add Verifiable Credential data to the blockchain even if it's encrypted, which minimizes the risk of unauthorized access. While encryption provides a level of security, it’s not foolproof.
Encryption is like putting your data in a locked box. It scrambles the information in a way that makes it difficult for unauthorized people to understand. However, with advancements in technology, there is a possibility that someone could find a way to unlock that box, even though it's difficult. Just like how new tools or techniques can be developed to open locks, technology can improve and make it easier to decode encrypted data.
2. Data Security
The way that blockchain is designed, data can’t be deleted off of the blockchain. That’s why putting personally identifiable information or Verifiable Credential information on the blockchain creates more risk of data exposure.
3. Reduces Cost
It’s expensive to store large amounts of data on the blockchain. By decentralizing data storage to personal devices, the need for resource-intensive blockchain infrastructure is minimized, leading to reduced operational expenses. Also the cost of maintaining and scaling the blockchain network is substantially lowered while still ensuring the security, privacy, and accessibility of Verifiable Credential data.
Why Blockchain Is Highly Fraud Proof

In a blockchain, information is stored in blocks, and each block has its own hash. The hash of a block is like a digital fingerprint of that block that acts as a unique identifier for that block.
But here's the cool thing: Each block's hash also includes the hash of the previous block. So, if someone tries to tamper with the contents of a previous block, the hash of that block will change. This, in turn, affects the hash of the next block, and the next, and so on. It creates a chain of interlinked blocks where any alteration to a single block will break the chain, making it obvious that something has been tampered with and the blockchain network will be notified.
This property of hash functions and linking blocks through hashes makes it extremely difficult to alter or manipulate information stored in a blockchain. It provides a strong layer of security and ensures the integrity and immutability of the data.
Dock’s Blockchain Certificate Verification System
Blockchain certificate verification is changing the way we trust and verify credentials. It is about making the process of validating certificates more secure, and efficient. When someone says they have a certain qualification or credential, they can prove it in an easy, reliable, and tamper-proof way.
Blockchain Certificate Verification Use Case Example

Let’s use an example to show the steps of how an issuer, holder, and verifier would use Dock’s blockchain verification system.
- Issuer: Work at Height training organization (ABC Training)
- Holder: Tyler Pozo
- Verifier: Fate Home Construction
1. Tyler creates a digital identity profile with his Dock Wallet which generates a DID (did:key).

2. After Tyler successfully finishes the Work at Height training course, ABC Training digitally signs the certificate of completion and sends the credential by email from Dock Certs. On the back end, the digital signature is done with ABC Training’s DID (did:dock) on the blockchain.

3. Tyler scans the QR code to import the credential into his Dock Wallet.

4. Tyler applies for a job with a construction company that requires Work at Height training. The construction company uses Dock Certs to make a request for his Work at Height credential by emailing Tyler a QR code that he can scan with his Dock wallet.

5. When Tyler scans the QR code, he accepts the verification request.

6. He is prompted to select the credential that has the requested information. In this case he selects his Work at Height training certificate.

7. Because ABC Training used Dock Certs to allow trainees to selectively share specific data to verifiers, Tyler chooses to only send his Work at Height license number and not other credential details like his full name and email to protect his privacy.

8. Tyler then chooses which digital identity profile he wants to use to present his credential.

9. The construction company instantly sees that the certificate is valid because of the efficiency of the blockchain verification process and they offer Tyler the job.

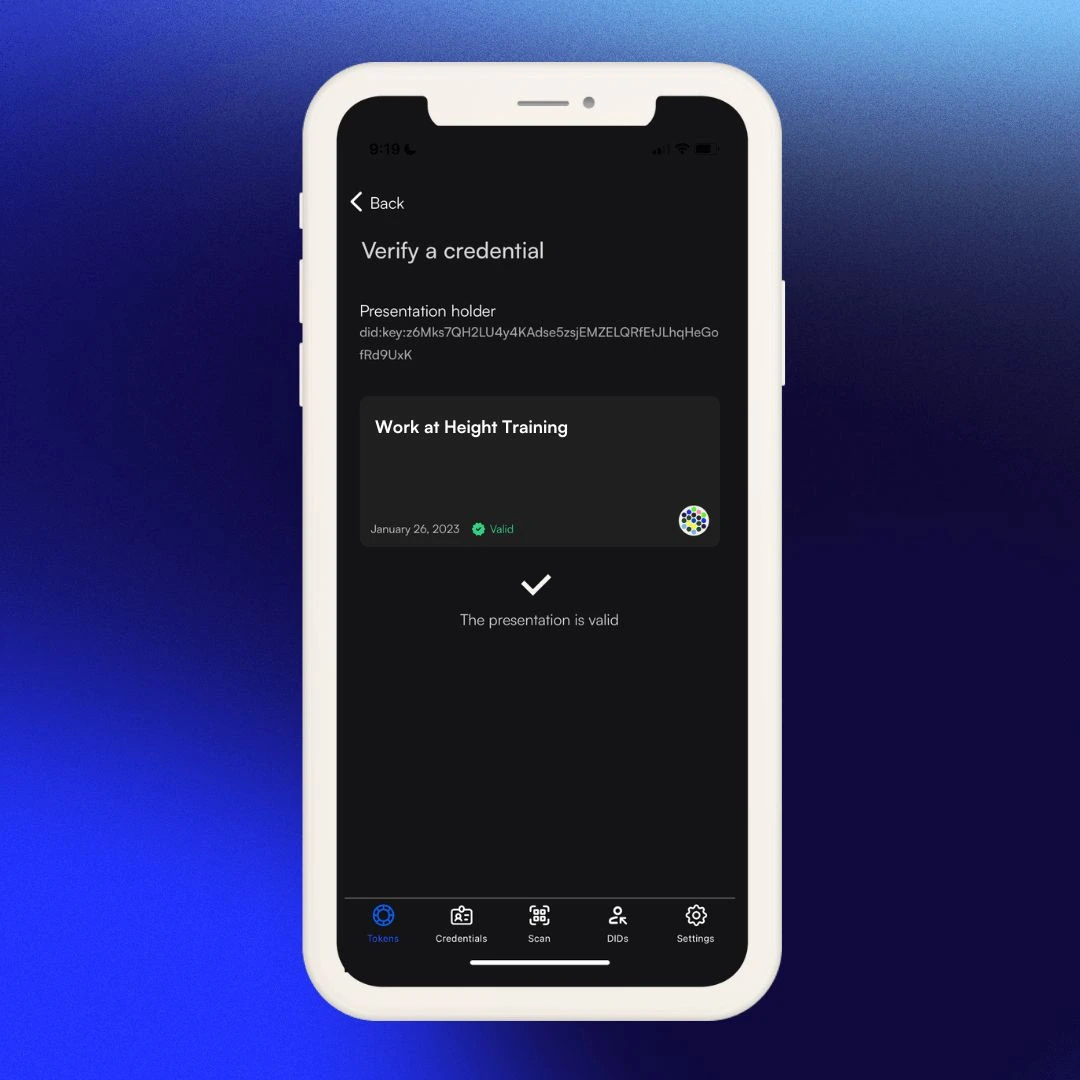
10. If Tyler tried to share a counterfeit certificate, the company would not be able to verify it since Dock's technology can identify fraudulent credentials. Dock can identify an invalid credential because Work at Height’s DID on the blockchain wouldn’t show up on the fake certificate. This is what Tyler would see on his wallet if he tried to send an invalid credential:

Blockchain Verification of Workforce Credentials

Problems With Traditional Verification Process
Verifying job applicants’ credentials is expensive and time-consuming. Traditional verification methods involve manual checks, phone calls, and emails to educational institutions, previous employers, and background screening agencies. These processes are not only time-consuming but also incur substantial costs for organizations.
Depending on how much information a company wants before hiring a new employee, background checks can range from $10 to $500 for each applicant. When you multiply the number of applicants, these expenses can add up quickly, especially for companies that often hire many employees.
Blockchain verification for job applicants is like having a trustworthy and unchangeable digital record of their qualifications and background. It makes the verification process faster, more reliable, and secure, benefiting both employers and applicants.
Benefits of Blockchain Verification for Organizations
- Data integrity: Employers can have confidence in the accuracy and integrity of the information they receive, as it has gone through a reliable verification process and issuer DIDs are stored on a tamper-proof blockchain.
- Faster verification: A company can conveniently request information such as the name of their university degree or professional certification details by sending a QR code for the job applicant to scan and present the information.
- Lower verification costs: The verification process is much faster, cheaper, and more efficient because the employer can check the validity of credentials without the need of intermediaries or long verification procedures like traditional methods.
Benefits of Blockchain Verification for Job Applicants
- Data privacy and control: Applicants can control access to their information. With Dock’s Selective Disclosure feature, the job applicant can choose to only share the information requested without revealing all of their details such as just their full name but not their mailing address if this privacy feature was enabled by the issuer such as a university. They can choose what information to share with employers and have the ability to grant or deny access to their credentials.
- Streamlined verification process: Instead of relying on traditional methods, which can involve multiple intermediaries, the decentralized nature of blockchain verification enables direct and efficient verification between the applicant and employer.
- Enhanced Security: Blockchain technology provides robust security measures which makes it extremely difficult for unauthorized parties to tamper with or forge verified credentials that are on users’ individual digital wallets. This helps protect applicants from credential fraud.

Conclusion
Blockchain verification ensures that credentials are authentic and tamper-proof. It offers a transformative solution to a variety of use cases to the common challenges of verifying credentials with traditional processes including being time-consuming, expensive, and vulnerable to fraud.
By leveraging decentralized identifiers and the power of blockchain technology, organizations can verify credentials instantly, be assured in the accuracy of the credential information, and lower verification costs. For individuals, they can present their credentials to verifiers while preserving their privacy and data security with the blockchain verification system.







