TL;DR
- A blockchain is a decentralized digital ledger that records transactions in a secure and transparent way. Instead of being stored in a centralized database, the information is stored across a network of computers, making it more difficult to hack or alter.
- There are two types of blockchains: public blockchain and private blockchain.
- A public blockchain is a type of blockchain that is open to anyone and can be accessed and verified by anyone on the network. Its key features and benefits include transparency, security, and decentralization.
- A private blockchain is a type of blockchain that is restricted to a group of participants who have been granted permission to access the network. Its key features include privacy and control. However, the downsides are that they are vulnerable to security risks, lack transparency, can be expensive to maintain, and centralized.
- Public blockchains are a better choice for organizations that want data security, privacy, transparency, and scalability. Data security is enabled by advanced cryptography and the decentralized nature of the chain as multiple copies are distributed across the blockchain network to ensure that manipulation can’t happen.
- To maximize data security and privacy, Dock never puts Verifiable Credential data and personally identifiable information on our public blockchain.
Blockchain is expected to grow from 4.93 billion USD in 2021 to 227.99 billion by 2028, a compound annual growth rate of 72.9% according to The Insight Partners. These figures include public, private, and consortium blockchains.
In this article we’ll go over:
- The key differences between public and private blockchains
- Address common misconceptions about public blockchains
- Why we built our own public blockchain at Dock
- How public blockchains can maintain security in industries that work with sensitive information such as finance, government, and healthcare
What Is a Blockchain and How Does It Work?

A blockchain is a decentralized digital ledger that records transactions in a secure and transparent way. Because it’s decentralized, it’s not controlled by any central authority, and operates on a peer-to-peer network of computers. Each block in the chain has a hash, which is like a unique digital fingerprint representing a specific piece of information that links it to the previous block, creating a chain of blocks that are virtually tamper-proof.
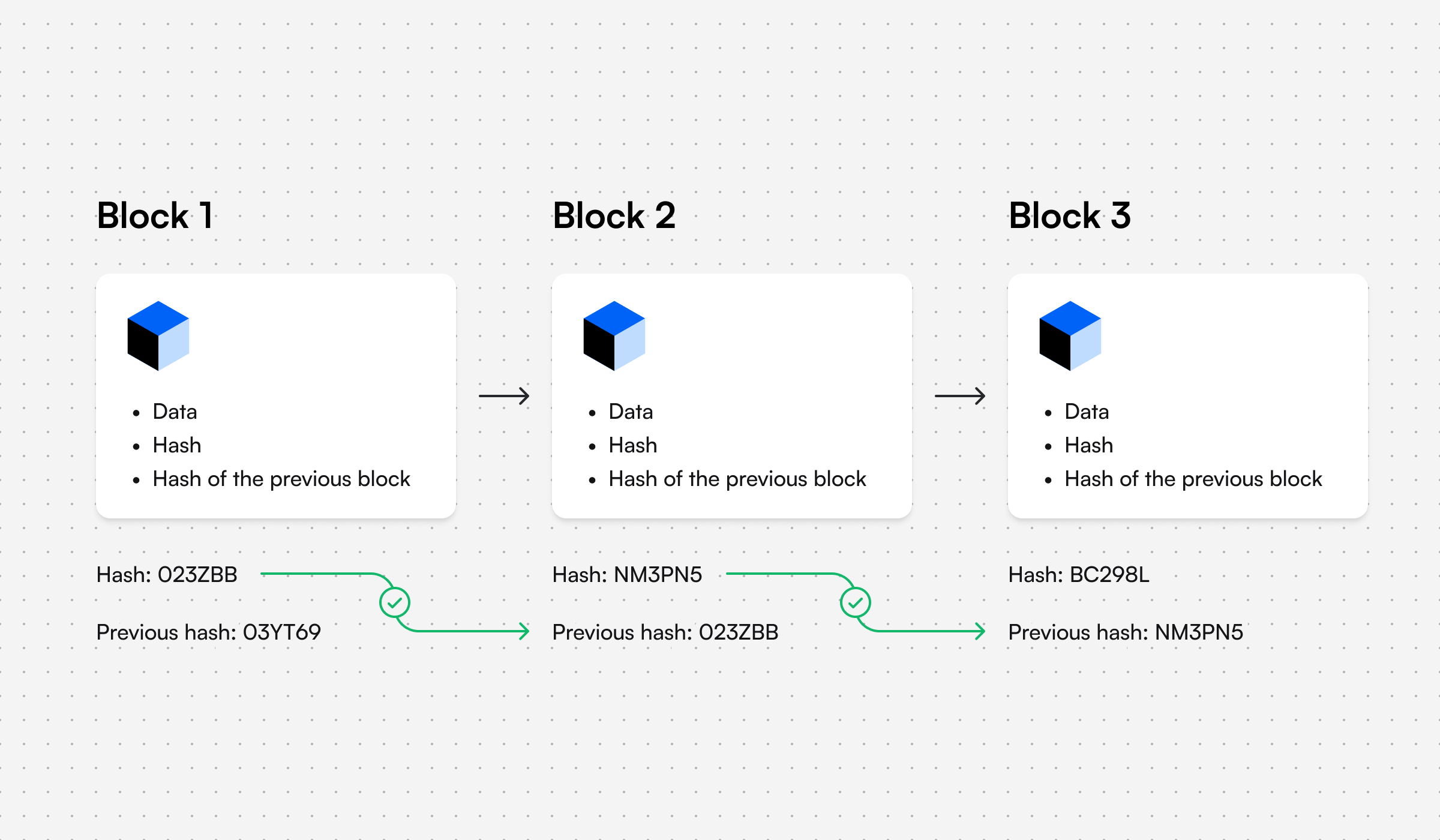
When a transaction occurs, it is verified by the network of nodes (computers) on the blockchain. Once the transaction is confirmed, it is recorded as a new block on the chain. Each node on the network has a copy of the blockchain, ensuring that everyone has access to the same information and that there is no single point of failure.
One of the key advantages of blockchain is its security. Because each block is linked to the previous block in the chain, it is extremely difficult to alter or manipulate any previous transaction data without being detected by the network. If someone tried to make a fraudulent transaction, the cryptographic block codes wouldn’t match and the network would be notified such as in this example:
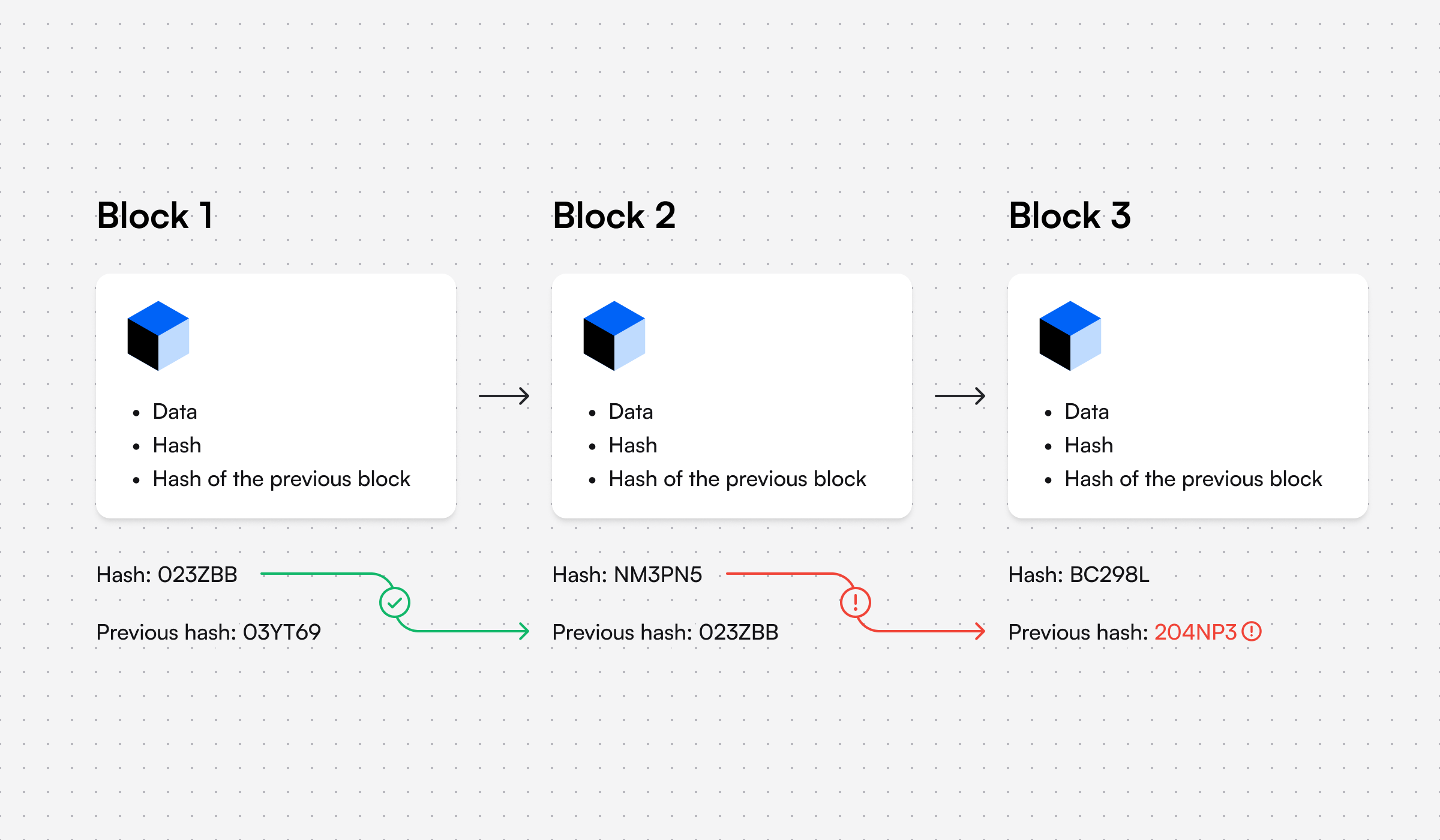
Blockchain solves many of the problems that often occur as a result of using traditional centralized digital databases and ledgers including:
- Being vulnerable to data security breaches because information is stored on a centralized server
- Less transparency and accountability because the information contained is controlled by a central authority
- User privacy can be compromised because the information can be accessed and used by a central authority
The Difference Between Public and Private Blockchains
Before going into more detail on public and private blockchains, here is a summary of between these two major types of blockchains.
What Is a Public Blockchain?
A public blockchain is a transparent, secure, and decentralized way of recording transactions on a digital ledger. It provides a powerful platform for creating decentralized applications and services that are accessible to anyone with an internet connection. Anyone can join the network, read the data, and participate in transaction validation. Examples of public blockchains include Dock, Bitcoin, and Ethereum.
What Are the Advantages of a Public Blockchain?

Accessibility: Public blockchains are accessible to anyone with an internet connection, regardless of location or background. This creates a more inclusive and open ecosystem where anyone can participate in the network and benefit from its applications.
Innovation: Public blockchains foster innovation by providing a platform for developers to create new applications and services that leverage the power of the network. This has led to the creation of a wide range of decentralized applications, such as digital identity and supply chain management solutions.
Security: Public blockchains use advanced cryptographic algorithms to secure and verify transactions and run on a decentralized network. These factors make them highly secure and resistant to attacks as any attempt to alter or manipulate the data on the network would be detected by the other nodes.
The more participants a blockchain has, the safer it is. As more people join the network, the number of nodes verifying each transaction increases. This makes it harder for a single malicious actor to manipulate the network because they would need to control a majority of the nodes in order to carry out a successful attack.
Transparency: Anyone can view and verify the transactions that occur on the network. This creates a high degree of trust and accountability since all of the parties involved in the network can see the same information.
Common Misconceptions About Public Blockchains
There is a common misunderstanding that public blockchains are not secure because anyone can view sensitive data. However, data can be well protected in the following ways:
1. Storing sensitive information on the blockchain requires data encryption before storing it. However, to maximize data security, this is not a practice that Dock implements as sensitive data is usually stored off chain.
2. If sensitive data is stored off chain, it can include a link and/or a cryptographic hash (like a digital fingerprint) of the data. An example of securing data linked to a blockchain is by issuing credentials such as identity documents, school degrees, and driver’s licenses as Verifiable Credentials.
Verifiable Credentials are a type of digital document that allow individuals and organizations to prove their identity, claims, and qualifications in a secure and decentralized way. The credential data is securely stored on individual user devices such as their phones with a digital wallet app rather than on the blockchain itself or centralized servers that can be vulnerable to data breaches.
They can be instantly verified by a trusted third party, such as a government agency or educational institution. Other examples of documents that can be issued as Verifiable Credentials include training certifications, employee status, and membership certificates.
3. If a Verifiable Credentials provider has Zero-Knowledge Proof technology features, users can confirm their details to verifiers without presenting any personal information at all such as confirming their age without showing their date of birth or confirming that they live in an eligible city for a government program without revealing their address.
How Digital Identity Management Works on Dock’s Public Blockchain

Verifiable Credentials and decentralized identifiers (DIDs) are technological tools for digital identity management that are commonly backed by public blockchains. They enable individuals to control their own identity data while still being able to prove their identity and claims.
Verifiable Credentials

Verifiable Credentials use advanced cryptographic techniques to ensure the security and privacy of the data while still being transparent and auditable with the use of decentralized identifiers (DIDs) which are stored on the blockchain. With Dock, Verifiable Credentials and personally identifiable information is never stored on our public blockchain.

Decentralized Identifiers (DIDs) for Digital Identity Management

Decentralized Identifiers (DIDs) are a way to create and manage digital identities that are independent of any centralized authority or organization. A DID is a unique identifier that is stored on a public blockchain, allowing individuals to control their own identity data and share it securely and selectively with others.
Here is an example of a DID created by the Dock Wallet:


The Risks of Adding Encrypted Data on the Blockchain

Data is often protected by encrypting it which means that it’s turned into a code that can only be read by someone who has the key to unlock it. Many organizations try to provide more data security by adding encrypted data to the blockchain to store and transmit sensitive information.
However, while encrypting data is an important security measure, it is not a foolproof solution. As computing power and technology continue to advance, encryption algorithms can become easier to break, making it possible for hackers to access sensitive data that has been encrypted. This is why Dock never adds Verifiable Credentials or personally identifiable information on the blockchain chain to maximize data security.


Dock vs. Other Blockchains
Here is a comparison of how Dock differs from other blockchains that provide Verifiable Credential and digital identity services, some of which are private blockchains.
We chose to build our own blockchain that is dedicated for decentralized digital identity use cases to better accommodate users. If our technology solutions were built using another blockchain, we would run the risk of being delayed by other applications running on the same blockchain.
Use Case Examples of Public Blockchains Maintaining High Data Security and Privacy
Because public blockchains have dominantly been used by cryptocurrencies to date, less people are aware of the growing number of use cases for public blockchains. Public blockchains provide a secure, transparent, and decentralized platform for a wide range of applications and industries including healthcare, finance, and government.
Healthcare
Electronic Health Records
Public blockchains can enable secure sharing of electronic health records between patients and healthcare providers with the explicit consent while still maintaining patient privacy and confidentiality. Patients would also be able to see who has accessed their data and for what purpose, increasing transparency and trust in the healthcare system.
For example, a patient's health record can be issued as Verifiable Credentials and the DIDs of each patient are stored on a public blockchain while the health record is kept on their digital wallet app like the Dock Wallet. This way of handling data helps health organizations meet data regulations like General Data Protection Regulation (GDPR), improve patient outcomes, and reduce medical errors while still maintaining the transparency and security of a public blockchain.
Improve Medical Supply Chains
Public blockchains can be used to improve the transparency and traceability across medical supply chains which reduces the risk of counterfeit products and improves patient safety. For example, a public blockchain could be used to track the movement of medical devices and medications from the manufacturer to the end user. Each step of the process could be recorded securely and transparently on the blockchain, enabling greater accountability and trust in the supply chain.
Finance
Digital Identity Verification
Public blockchains can also be used for digital identity verification and improve the privacy of customer data while still being transparent. For example, a public blockchain could be used to store customer DIDs in order to enable instant ID verification of their digital identity documents that are issued as Verifiable Credentials such as driver’s licenses and government-issued ID documents. This approach to ID verification reduces the risk of identity theft and fraud.
Customers would hold their credentials securely in their digital phone wallets rather than a centralized server and the financial institute reduces their risk of holding a large amount of customer data that can be vulnerable to large-scale data breaches.
Cross-border payments
Public blockchains can be used to securely transfer funds across borders, reducing the risk of fraud and increasing trust in the financial system. For example, a public blockchain could be used to record and verify the transfer of funds between banks or other financial institutions. This would allow for greater accountability and transparency in the transfer process.
Government
Identity Documents
Public blockchains can also be used to securely issue and verify identity documents such as passports and driver's licenses. With Verifiable Credentials and DIDs, individuals have full control of when and who they want to share their information with. Credential verifiers can’t access their information without explicit consent.
Public Records
Governments can issue public records such as property deeds, identity documents, and birth certificates as Verifiable Credentials that people can securely store on their digital wallet. If, for example, there’s a real estate transaction that requires different credentials, a bank offering a loan could request different credentials such as a full name, date of birth, and job salary by sending a QR code to the borrower. A property buyer would then be prompted on their Dock Wallet app to give permission to share the relevant credentials.
Our Response to Cited Disadvantages of Public Blockchains
The following points are often mentioned as the downsides of public blockchains but there are developments that are solving the problems.
Scalability
Many people believe that public blockchains can be slower and less scalable than private blockchains, as each transaction must be verified by a network of nodes. This can lead to slow transaction times and high fees during times of high network traffic. While this is true for blockchains that use a Proof of Work validation system such as Bitcoin, public blockchains have had major developments in different scalability solutions, particularly blockchains like Dock that use a Proof of Stake validation system that can scale as needed.
Proof of work (PoW) is a system where a computer must perform a complex mathematical calculation, known as "mining," in order to validate transactions and add new blocks to the blockchain. This process requires a lot of computational power, which makes it difficult for any one user to manipulate the system. It also consumes a lot of energy and can be slow.
Proof of stake (PoS) is a newer system where users "stake" a certain amount of cryptocurrency to become validators on the network. Validators are chosen based on the amount of cryptocurrency they hold, and they use that cryptocurrency as collateral to verify and validate transactions. The more cryptocurrency a user stakes, the more likely they are to be chosen as a validator. With this validation system, PoS can enable blockchain scalability by reducing energy consumption and increasing transaction speed since it doesn’t require the same level of computational power as PoW.
Privacy
Public blockchains are transparent, meaning that anyone can view and trace the history of transactions on the network. Many people are concerned that this can be a disadvantage for applications that require privacy and confidentiality.
However, there are different ways to maintain a high degree of privacy and confidentiality. In addition to using Verifiable Credentials, off-chain data can be linked to a public blockchain by storing a hash of the information on the blockchain. By storing the hash, anyone can verify that the information has not been modified off-chain, as any changes to the original data would result in a different hash.
For example, a company could store customer data off-chain in a secure database, but store a hash of that data on a public blockchain. This would allow anyone to verify the authenticity of the customer data by comparing the stored hash to the hash of the current data.
Energy consumption
Public blockchains, particularly those that use Proof of Work consensus algorithms, can require significant amounts of energy to maintain the network. This can have negative environmental impacts and results in high costs for users.
In contrast, PoS blockchains have much lower energy consumption and carbon footprint than PoW blockchains, making them a more environmentally friendly option. Because PoS blockchains do not require vast amounts of computing power to validate transactions, they consume far less energy.
Governance
Many people think that public blockchains can be difficult to govern because they are run by a network of computers with no single point of control. This can lead to issues with decision-making, coordination, and updates to the network. While these problems may be true in some cases, blockchains can be effectively governed in a way that doesn’t necessarily need to be difficult and inefficient.
Public blockchains rely on a community of users and stakeholders to make decisions about the network. This means that decision-making is decentralized, with each participant having a say in the direction of the network. While this can sometimes lead to disagreements and debates, it also ensures that decisions are made with the best interests of the community in mind.
Also, because the network is decentralized, there is no single point of failure that can be exploited by bad actors. There are built-in incentives to encourage good behavior and discourage bad behavior in PoS blockchains where stakers are rewarded for holding and staking cryptocurrency. These incentives help to align the interests of network participants and encourage them to act in the best interests of the network.
What Is a Private Blockchain? (AKA Permissioned Blockchain)

A private blockchain is a decentralized ledger that is only accessible to a select group of individuals or organizations. It has a single operator or entity that controls who can access the network, view information, and create data on the blockchain. To gain access to a private blockchain network, individuals must receive an invitation and verify their identity or provide the necessary information.
Unlike public blockchains where the identity of people are largely anonymous, the identity of people involved on a private blockchain is known. Examples of private blockchains include Hyperledger and Corda. Only selected users may maintain the shared ledger while the owner can override, edit, or delete entries on the blockchain as they see fit.
The network operator(s) or a set protocol approved by the network use smart contracts or other automated methods to authenticate and verify the participant's details. When someone wants to make a transaction on a private blockchain, they submit it to the network for verification. Once the transaction is confirmed by the nodes, it is added to the blockchain as a new block.
Why Some Organizations Use Private Blockchains
In contrast to a public blockchain, a private blockchain is a closed database that uses cryptography to ensure security and comply with the organization's requirements. Many enterprises use this option to keep some or all of their transactions private or only for internal uses.
With private blockchains, efficiency and immutability are prioritized over the safeguarding of user identities and transparency. Because they have less users in the centralized network, they can process more transactions because less time is needed to reach a consensus to validate a transaction.
Disadvantages of Private Blockchains

Security risks: While private blockchains are more secure than traditional databases, they are much more vulnerable than public blockchains to security risks because there are fewer nodes (computers) in the centralized network. If a hacker gains access to a private blockchain, they can manipulate data or block transactions.
Lack of transparency: Private blockchains prioritize privacy, which means they are not transparent. This lack of transparency can make it difficult to verify the accuracy and authenticity of the data on the blockchain.
Cost: Private blockchains can be expensive to set up and maintain because it requires a certain amount of computing power and data storage. As a result, the costs will go up as the amount of data grows. In contrast, with public blockchains the costs are distributed to everyone running a node and the rewards cover the costs.
Centralization: Private blockchains are often centralized where a single organization controls the network. This centralization can be problematic since it goes against the core principle of decentralization, which is one of the fundamental concepts of blockchain technology.
Do Organizations Need to Use Private Blockchains at All?
Avivah Litan, the Vice President and analyst of Gartner, a reputable research and consulting firm for businesses in the IT sector, wrote a report that said that in the last few years, only 14% of private blockchain projects went into production. Among those that went to production, they were distributed to a limited number of nodes on the private blockchain and also had low transaction volume which led to many people wondering if they even need to use blockchain technology at all.
Litan said, “These projects did not have to use a private blockchain distributed ledger technology. Instead, they could have used a centralized ledger or even a regular database.” Given the limitations of private blockchains, Litan predicted that “Standalone private blockchains will go away. But smaller, niche private blockchains that attach to public blockchains are more likely to remain.”
David Treat, the Managing Director and Co-lead of Accenture’s blockchain business unit, suggested that organizations “What you want to do is line up the functionality, expectations, rules, governance regulations and technical characteristics of what you want to build and then build a system that can match those requirements.” The system that matches their requirements may or may not require blockchain.
Other Types of Blockchains
Hybrid Blockchain
A hybrid blockchain is a type of blockchain that combines elements of both public and private blockchain. It allows for a mix of open and restricted access to the network, depending on the use case and application.
For example, a company could put their data on a private blockchain to keep the information confidential but add a digital fingerprint of the data on a public blockchain to secure it. If someone suspects that the data may have been manipulated and wants to investigate, they can compare the information on the private blockchain with the public blockchain fingerprint.
Consortium Blockchain (AKA Federated Blockchain)
A consortium blockchain is a type of blockchain where multiple organizations or entities come together to form a network, and each participant has a role in verifying and recording transactions on the network. This differs from private blockchains where a single entity controls the network and from public blockchains where anyone can join the network.
In a consortium blockchain, each participant has an equal say in the governance and operation of the network. Transactions are verified and recorded through a consensus mechanism where all participants must agree on the validity of each transaction before it is added to the blockchain. This ensures that the network is secure, transparent, and tamper-proof, while still maintaining a degree of control and privacy for the participants.
Organizations that often use this type of blockchain are those that need to do organizational collaboration. However, it’s less transparent and less anonymous compared to anonymous blockchains.
Conclusion
Blockchain technology has the potential to revolutionize the way we store and transmit sensitive data. There are two major types of blockchains: public and private. Public blockchains offer more accessibility, innovation, security and transparency while private blockchains provide more control and privacy.
Public blockchains can be used for a variety of use cases, including industries that require high data security and privacy such as healthcare, finance, and government. By using advanced cryptographic techniques and Verifiable Credentials, public blockchains can securely store and transmit sensitive information.
At Dock, we never put Verifiable Credentials or personally identifiable information on our public blockchain. Instead, we use decentralized identifiers (DIDs) to enable users to securely store data on their personal devices and organizations to instantly verify the authenticity of their credentials.
About Dock
Dock is a Verifiable Credentials company that provides Dock Certs, a user-friendly, no-code platform, and developer solutions that enable organizations to issue, manage and verify fraud-proof credentials efficiently and securely. Dock enables organizations and individuals to create and share verified data.
Dock’s Solutions
- Dock Certs: Web app to issue and manage digital identity and Verifiable Credentials
- Certs API: Easy integration with your system to make your data fraud-proof and instantly verifiable
- Dock Wallet: Easily store and manage their digital credentials and identity (individuals) and verify credentials instantly (organizations)
Partner Use Cases
- SEVENmile issues fraud-proof verifiable certificates using Dock
- BurstIQ Makes Health Data Verifiable, Secure, and Portable With Dock
- Gravity eliminates Health & Safety certificate fraud with Dock
Learn More
- Decentralized Identity
- Verifiable Credentials
- Self-Sovereign Identity
- Decentralized Identifiers (DIDs)
- Web3 Identity
- Blockchain Identity Management
- Selective Disclosure
- How to Prevent Supply Chain Fraud With Blockchain
- BurstIQ Use Cases That Leverage Verifiable Credentials
- Blockchain Food Traceability: Enhancing Transparency and Safety
- What Are Digital Credentials?
- Data Compliance
- How to Prevent Certificate Fraud
- Digital Credential Platform







